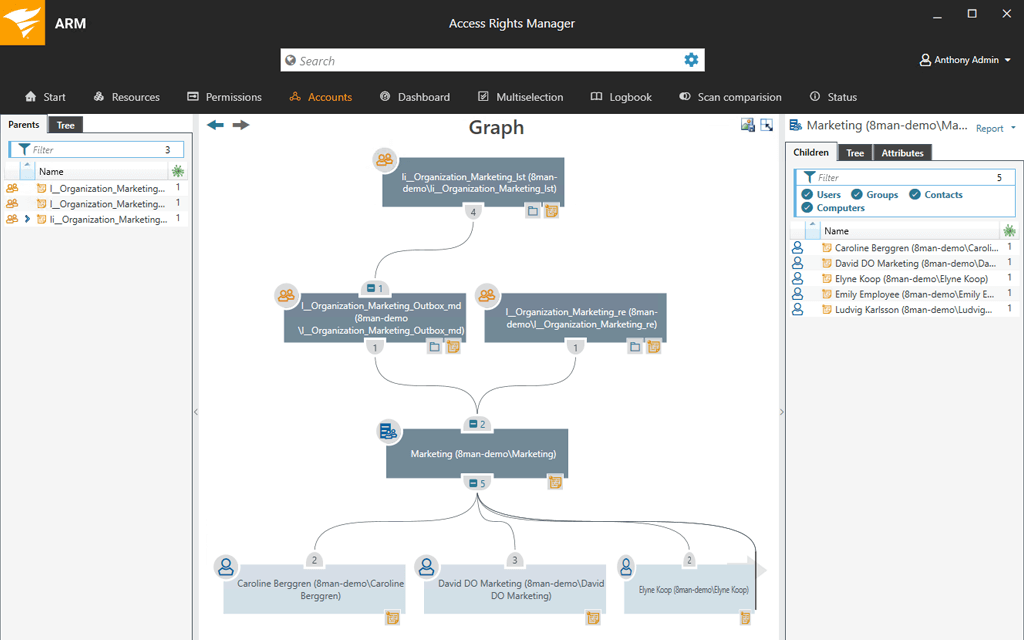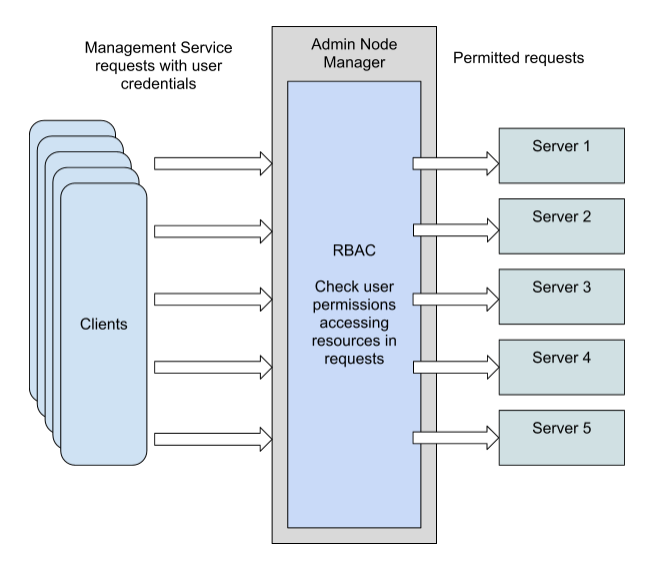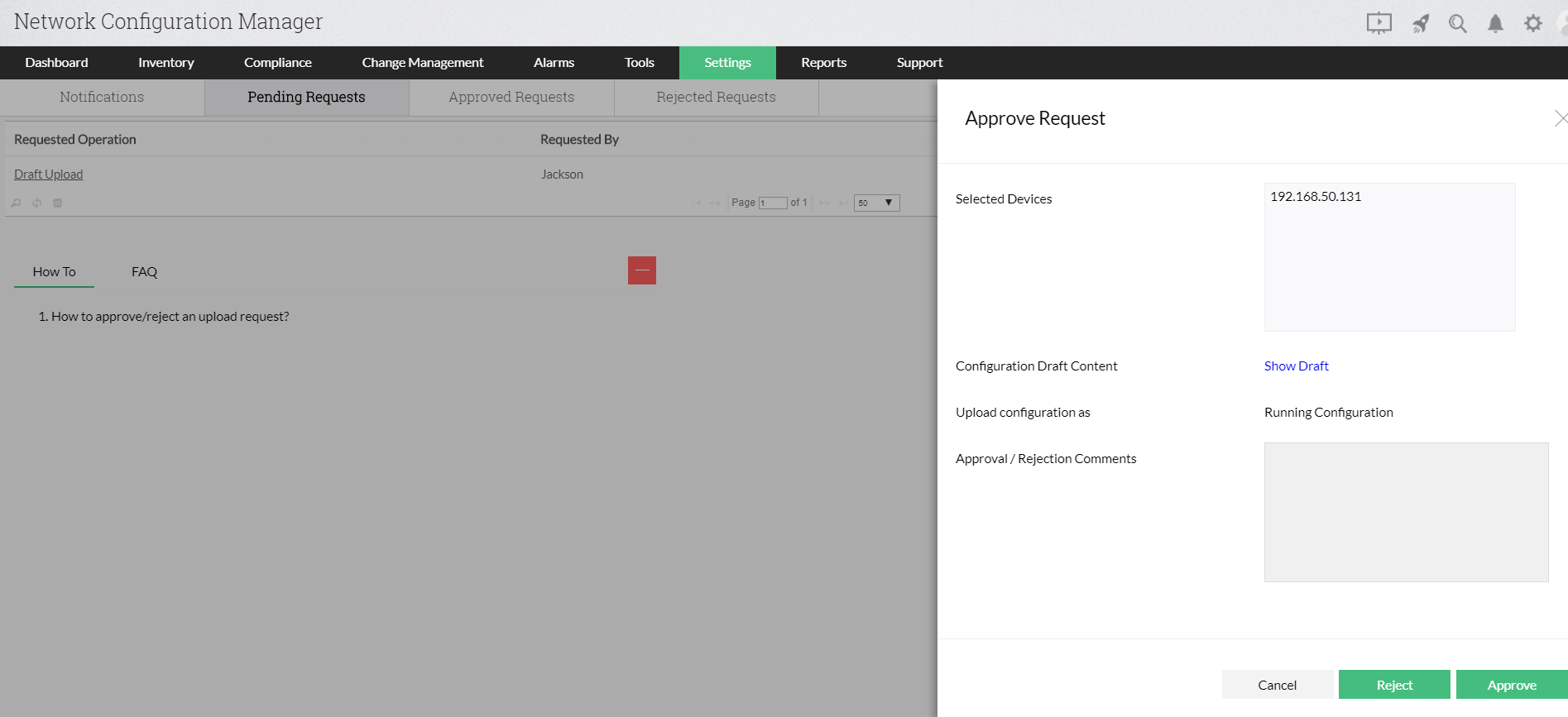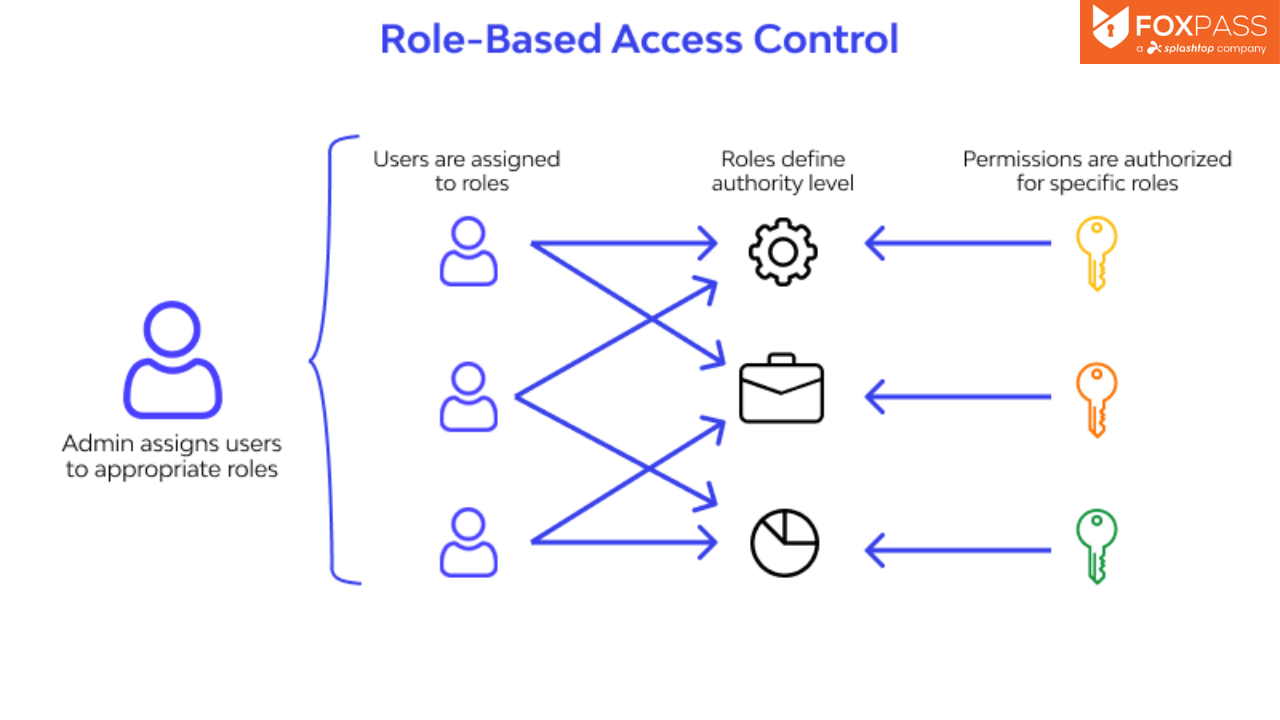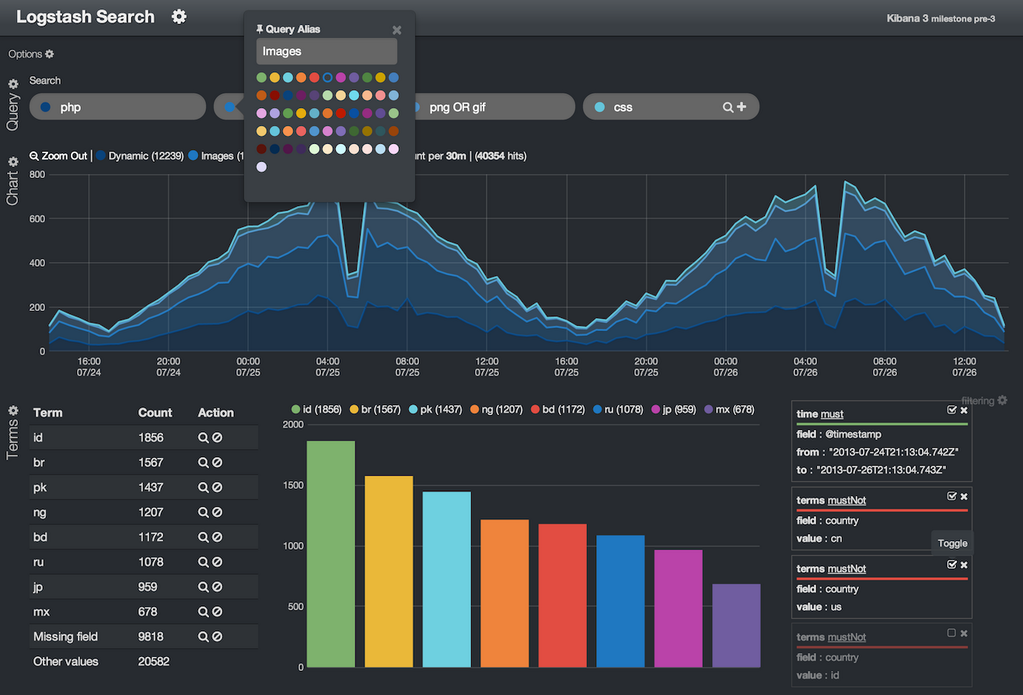
Role Based Access Control (RBAC) in Elastic Stack – BGD e-GOV CIRT | Bangladesh e-Government Computer Incident Response Team

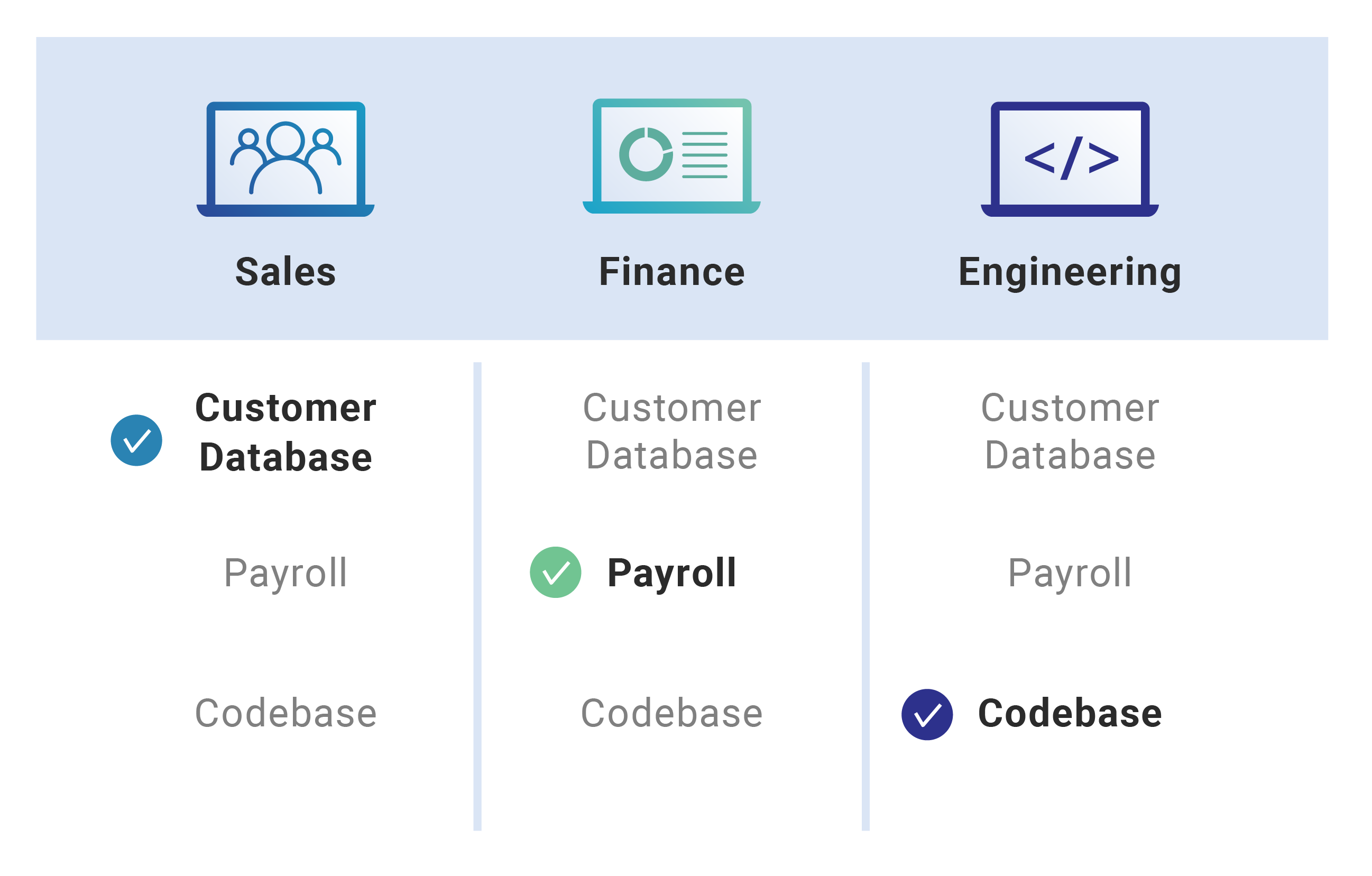
How to Implement fine-grained Role-Based Access Control for Your Infrastructure as Code with Custom RBAC Roles | env0
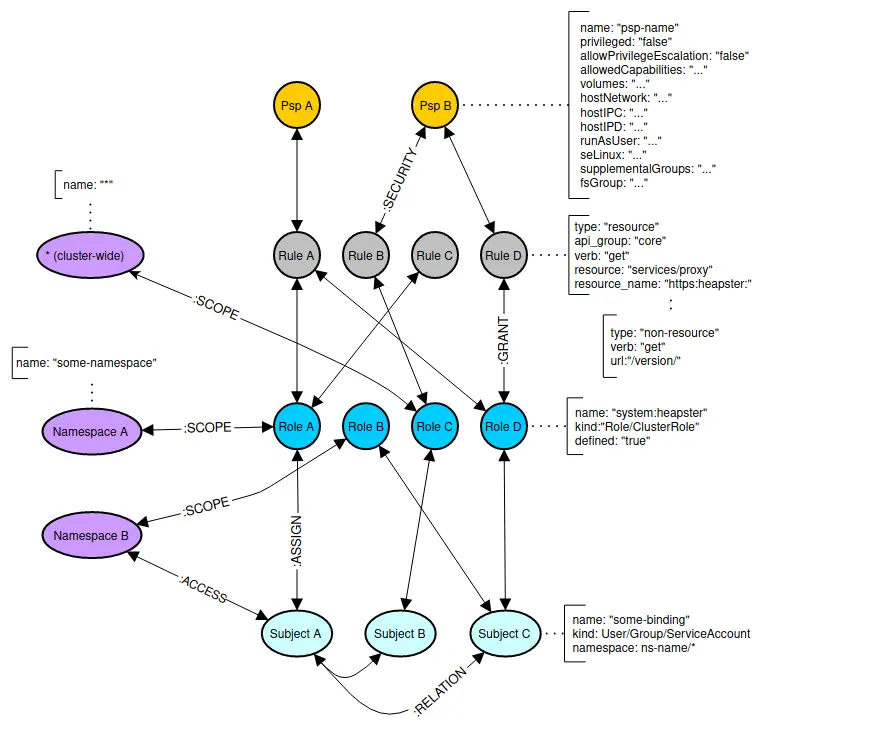



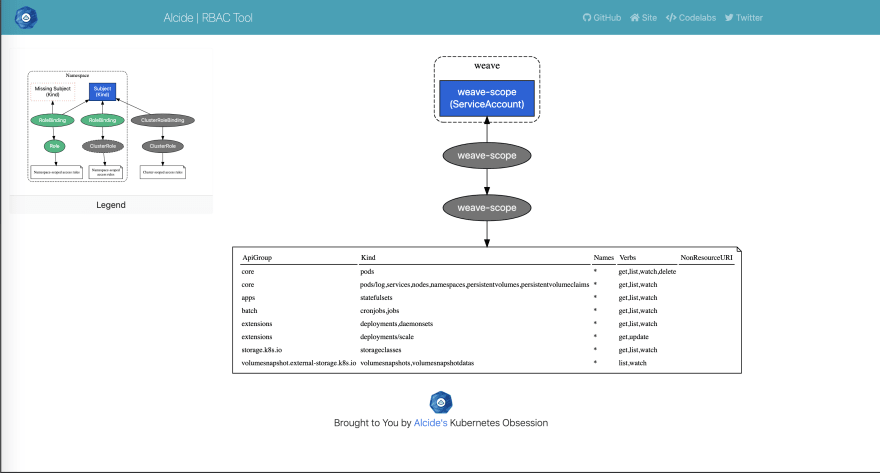

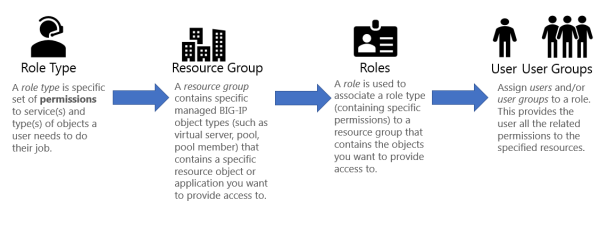

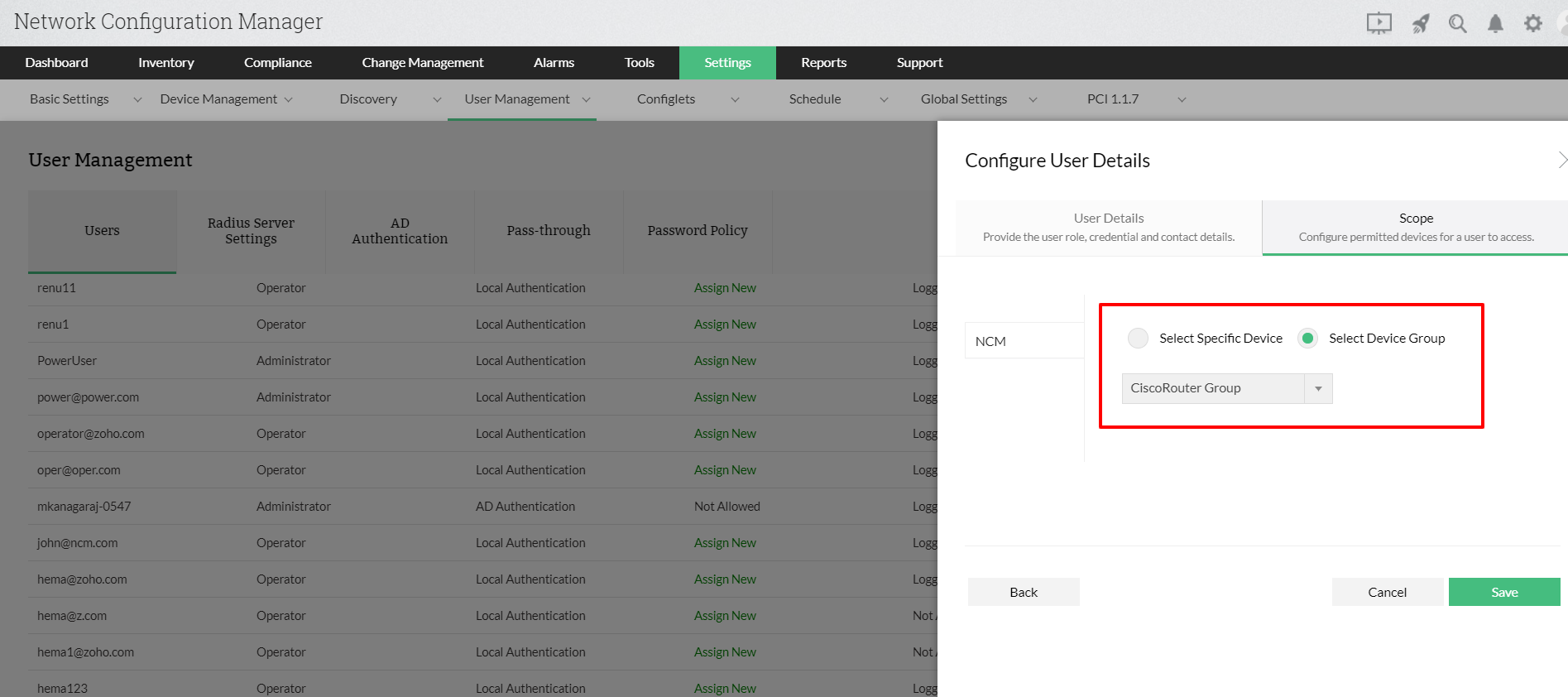
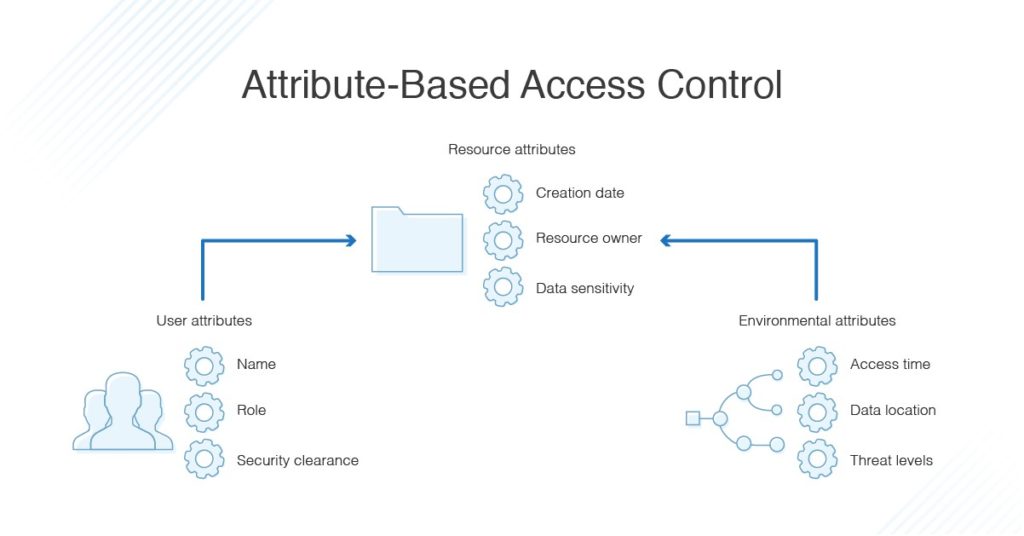
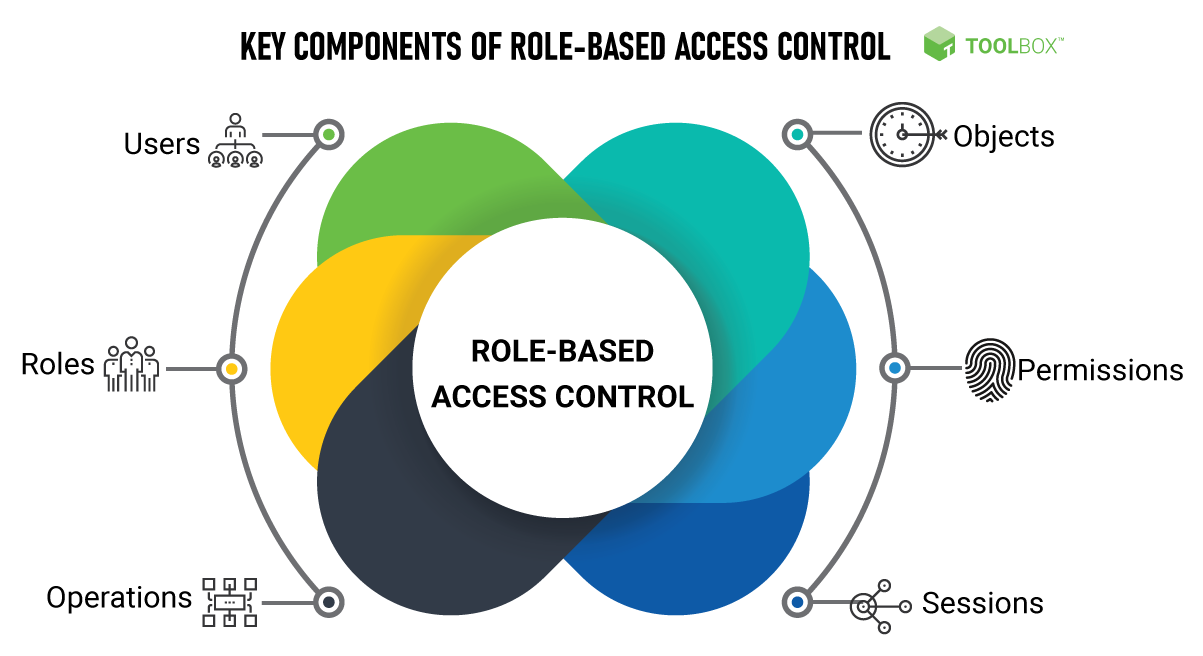

![PDF] A Role Engineering Tool for Role-Based Access Control | Semantic Scholar PDF] A Role Engineering Tool for Role-Based Access Control | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/0e9fed33361980b50cac79c71e1beec24a0d9141/1-Figure1-1.png)